
By Dave DeWitte
dave@corridorbusiness.com
Editor’s note: This is the first in a CBJ-exclusive series exploring digital privacy and its ramifications for companies and employees, available first to CBJ members.
Technology wonks have been debating the death of privacy for years, as innovations from web browsers to websites to social media collected more and more of users’ personal data, and as news of data breaches became commonplace.
“Privacy – will it ever stop dying?” quips a popular bumper sticker.
But in recent years, that slow-motion death has quickened, and become nearly impossible to ignore.
The first shocking consumer breach of the new era was in 2013 at Target, where hackers made off with the credit card information of 41 million customers. The massive Equifax breach of 2017, in which the personally identifiable information (PII) of 147 million Americans was stolen, cemented the issue in consumers’ minds.
Topping that seemed impossible, but this year has proven otherwise. It began with a disclosure that PII from 247,167 employees of the U.S. Department of Homeland Security, and individuals under investigation by that department, had been stolen over a 12-year period.
In March, hackers infiltrated and locked down the city of Atlanta’s computer system and held the city’s data systems hostage over demands for $51,000 in bitcoin.
The Cambridge Analytica scandal blew up the same month, with revelations that Facebook allowed the data of some 87 million Americans to be mined and sold for political use, ultimately ending up in the hands of Russian intelligence services. Problems with foreign interference on the platform resurfaced in July, when Facebook shut down dozens of “inauthentic” profiles and pages set up to sow disinformation ahead of the fall election cycle.
The wave of bad news arrived in the Corridor in July, when Iowa’s largest medical care system, UnityPoint Health, disclosed that the PII of 1.4 million patients contained in emails or attachments may have been compromised through “phishing” attacks aimed at employees and designed to look like they were from a UnityPoint executive. The emails and attachments may have contained information about patients’ diagnosis, treatment, surgery, lab results, dates of services and insurance, the health system said in a letter, in addition to basic PII such as Social Security numbers and birthdates.
No misuse of patient information was reported, the letter maintained, and it appeared that the perpetrators were trying to divert payroll or vendor payments.
And the drumbeat continues: Chinese hackers stole secret plans for a new U.S. naval weapon from government contractors. Iranian hackers were indicted for hacking the accounts of 8,000 university professors, stealing intellectual property and large amounts of data. Delta Airlines, Reddit.com and Sears have all reported PII taken in data breaches this year.
What all of these incidents have in common is the growing tactical and technological race between those with data they want to protect, and those who want to steal data for their own financial, tactical or personal gain. In short, cybercrime has become institutionalized and systematized.
“Criminal [data theft] enterprises are now worth $1 billion and they’re turning that money around on R&D so they can be better,” said Marc Goodman, author of the book “Future Crimes,” during a June presentation at the Iowa Association of Business and Industry’s conference in Coralville.
International intrigue
Much of the large-scale data theft has been conducted by state-sponsored enterprises, some of it for economic gain and some of it for geopolitical advantage.
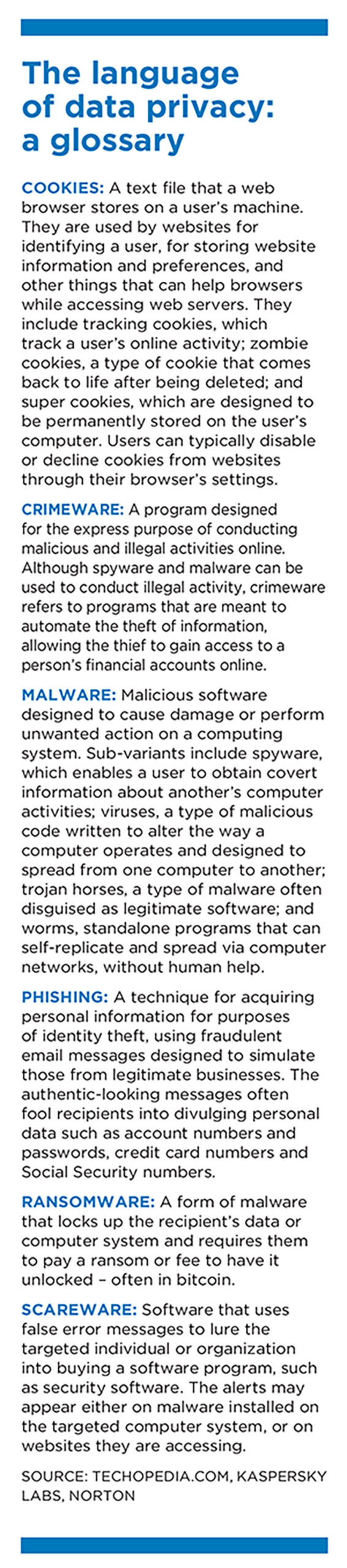 North Korea was behind a major ransomware attack in May that hit computers worldwide, Gen. Vincent Brooks, commander of U.S. Army forces in South Korea, told a Senate subcommittee in March. The country has more than 6,000 hackers whose “improving capabilities provide the regime with a financial pipeline to support its weapons programs and a means to collect sensitive information from other parties and disrupt infrastructure in other countries,” he said.
North Korea was behind a major ransomware attack in May that hit computers worldwide, Gen. Vincent Brooks, commander of U.S. Army forces in South Korea, told a Senate subcommittee in March. The country has more than 6,000 hackers whose “improving capabilities provide the regime with a financial pipeline to support its weapons programs and a means to collect sensitive information from other parties and disrupt infrastructure in other countries,” he said.
In 2016, Mr. Brooks noted, North Korea’s cyber forces were able to steal more than $80 million from international financial systems.
Russia’s cyberwarfare capabilities have been in the news almost weekly as a result of the FBI’s probe into Russian interference in U.S. elections. Microsoft’s revelation in August that it had shut down web domains set up by the Russians to influence the midterm elections this fall served as the latest reminder of the country’s efforts.
In a recent report, the nonprofit research and analysis organization CNA said information warfare has become a standard and accepted part of Russia’s international relations and military strategy. China, meanwhile, is developing advanced information warfare as a vital component of its military strategy, according to a 2016 report by the National Security Agency.
“China is likely using its maturing computer network exploitation capability to support intelligence collection against the U.S. government and industry by conducting a long-term, sophisticated computer network exploitation campaign,” the report said.
These operations use sophisticated techniques, access to high-end software development resources, deep knowledge of the networks targeted and the ability to sustain activities inside the targeted networks for months, it added.
Analysis of the Chinese intrusions indicate the use of Chinese “black hat programmers” – freelance individuals who support illegal hacking activities – for the creation of customized tools that exploit vulnerabilities in commercial software that vendors have not yet discovered, the NSA reported.
Business IT resources connected to the Internet are “constantly being probed at the top-level architecture level for vulnerabilities,” said Shadrack Roberts, cybersecurity and data privacy officer for the U.S. Army Sustainment Command at the Rock Island Arsenal.
Even so, Mr. Roberts told an audience at this year’s EntreFEST in Cedar Rapids that the most catastrophic damage he’s seen during his career came from insider threats, often motivated by personal resentments or a desire for financial gain.
Some Corridor businesses truly are high-profile targets in the unfolding age of cybercrime. Staying ahead of the threat is a priority for the Corridor’s largest employer, Rockwell Collins. Soon to become part of United Technologies’ Collins Aerospace Systems unit, Rockwell Collins supplies the electronics used to navigate and communicate with aircraft in an increasingly networked aviation world. Kent Statler, executive vice president of the company’s Commercial Systems division, says cybersecurity is one of the skillsets in the highest demand at Rockwell.
“When you start talking about aircraft being hacked, you’ve got a personal fear factor that’s hard to quantify,” Mr. Statler acknowledged at the CBJ’s Mid-Year Economic Review in July, adding “We test our systems on a daily or at least weekly basis. It’s very safe to fly.”
The emerging Internet of Things is opening new fields of opportunity for hackers, who have already developed ransomware for smart TVs and digital home thermostats, according to author Marc Goodman. He called for a “new Manhattan project” to stem the growing threat with federal leadership.
Tools of the trade
Just how pervasive have cyberattacks become? Consider that the percentage of cyberattacks that become known to the public is likely to be a fraction of the total. When Greg Edwards operated a Cedar Rapids-based data backup firm, he said 20 percent of his clients were targets of cyberattacks during a three-year span from 2012-2015.
Hackers are now using sophisticated tools stolen from the CIA and the National Security Agency in late 2016, and offering them to others.
The hacker group known as the Shadow Brokers offered the tools for sale to other hackers in exchange for untraceable bitcoin. They included tools designed to help malware evade detection, redact event logs in Windows systems and exploit the Server Message Blog on Windows systems in such a way that it could be used to control a computer remotely, according to a report from the security consultancy SentinelOne.
The trade in “crimeware” includes tools developed by criminal syndicates themselves, according to Mr. Goodman, a former senior advisor to Interpol. An example Mr. Goodman has cited is Innovative Marketing Ukraine, which was prosecuted by the Federal Trade Commission in a series of actions that began in 2008. The company developed “scareware” that deceived internet users into thinking their computers were infected with viruses to convince them to download malware disguised as antivirus software.
The malware hijacked users’ web browsers and deceived hundreds of thousands into disclosing their credit card information. According to the FBI, Innovative Marketing probably bilked users out of more than $100 million before it was shut down.
Although Innovative Marketing has gone away, its crimeware products haven’t.

“I don’t think any business ever feels safe anymore, and they shouldn’t,” concludes Mr. Edwards, who is now CEO of WatchPoint, a data security company based in Cedar Rapids.
Organizations that use data typically only disclose breaches to meet regulatory or legal requirements.
“The breaches you learn about on TV – that’s 1 percent of the total,” Shadrack Roberts said. “Most [victims] don’t want to expose themselves – it’s a liability factor.”
There are good reasons why organizations don’t disclose more breaches. The reputational harm of disclosing a breach can be costly to businesses, according to Mr. Edwards, and the odds of recovering losses through prosecutions is usually not good.
“The FBI is so overwhelmed, they can’t investigate every incident,” said Mr. Edwards. “They’re focusing on the Equifax attacks and big break-ins, not the accounting firm that lost 200,000 records in Iowa.”
The use of ransomware to lock down a victim’s data and hold it hostage has become more common. But even victims of ransomware attacks often don’t report it, because the attackers typically don’t ask for vast amounts.
“Most ransomware requests were for a few hundred dollars,” Mr. Edwards said. “They just wanted to get paid, and now it’s up to over $600.”
Looking inward
Personal privacy is a corollary issue of data privacy. Criminals can use private information they obtain on employees to manipulate behavior, or even to blackmail them.
The concept of privacy itself is rapidly eroding as more and more information is collected on individual behavior, and not just by putting cookies on web browsers.
“The whole idea of personal privacy is almost a facade,” Mr. Roberts said. “If you’re carrying a smartphone, you’re carrying a microphone, a video recorder, an audio recorder and a geotracker.”
The Pew Research Center conducted a two-and-a-half-year study evaluating the changing attitudes of Americans following revelations of government spying in the 2013 NSA data leak involving government contractor Edward Snowden.
An overwhelming 91 percent of adults agreed or strongly agreed that consumers have lost control of how personal information is collected and used by companies.
“Americans express a consistent lack of confidence about the security of everyday communication channels and the organizations that control them – particularly when it comes to the use of online tools,” said a summary of the report. “And they exhibited a deep lack of faith in organizations of all kinds, public or private, in protecting the personal information they collect.”
The least trusted organizations in the survey were online advertisers, followed by social media sites, online sites and search engine providers. The most trusted were credit card companies, government agencies and telephone companies.
UP NEXT: The digital finger in the dike
The question about data breaches is not “if” but “when.” The CBJ explores how security precautions and other steps to reduce liability can make the difference between an existential crisis and a temporary setback. Look for the next installment in our Death of Privacy series in the Oct. 8 edition of the CBJ.




